Blogs

The Hidden Cost of Your Digital Footprint
The Hidden Cost of Your Digital Footprint April 1, 2025Every year on April 22, we celebrate Earth Day, a global…

Spring Clean Your Devices
Spring Clean Your Devices & Protect Your Data March 3, 2025Spring is the perfect time to declutter your home, but…

Stay Protected During Tax Season
Stay Protected During Tax Season January 6, 2024Tax season is here, and while you’re busy crunching numbers and filing returns,…
Prioritize Your Credit During Financial Wellness Month
Prioritize Your Credit During Financial Wellness Month January 6, 2024January is Financial Wellness Month, a perfect reminder to take control…

End The Year Securely
End the Year Securely: Your Identity Protection Checklist December 4, 2024As the year winds down, it’s the perfect time to…

Protect Yourself from Holiday Shopping Scams with IDSeal
Protect Yourself from Holiday Shopping Scams with IDSeal November 4, 2024The approaching holiday season means a surge in online shopping…

The True Cost of Identity Theft: How Identity Theft Protection Saves You Time and Money
The True Cost of Identity Theft: How Identity Theft Protection Saves You Time and Money October 07, 2024Identity theft is…

Decoding the Dark Web: How Your Data Could End Up in the Wrong Hands
Decoding the Dark Web: How Your Data Could End Up in the Wrong Hands September 11, 2024Though so much of…

Identity Theft Can Have a Profound Impact on Employee Performance
As we celebrate Independence Day this month, it’s a perfect time to reflect on the true essence of independence. Just…

IDSeal® allows you to independently manage your identity
As we celebrate Independence Day this month, it’s a perfect time to reflect on the true essence of independence. Just…

Shield Your Family with IDSeal® Family Plans
As the sun shines brighter and the days longer, it’s clear that summer is just around the corner. For many,…

Navigating the High Seas of Online Travel Booking
As the sun shines brighter and the days longer, it’s clear that summer is just around the corner. For many,…

Secure Connectivity with Pro-Tec VPN
A Virtual Private Network (VPN) is a service that encrypts your internet connection, securing your online activities from cyber threats.…

Identity Theft Explained
What is identity theft? Identity theft is when someone steals your personal information and uses it without your permission to…

Taxpayer Beware: Stay one step ahead of savvy scammers
Tax season is often met with dread by Americans. For many, it is that familiar feeling that, yet again, unjoyful…

10 Simple Ways to Protect Yourself From Identity Theft
According to a study from Verizon, 74% of successful cyberattacks or unintentional data leaks stemmed from social engineering, human error, or…

How to Avoid Online Shopping Scams This Holiday Season
As fall fades into winter and the holidays approach, a sense of wonder descends like the first snow. This time…

How Artificial Intelligence Enhances Social Engineering Attacks
Voices are a unique way to identify someone. So much so that babies know their mother’s voice early in development…

How Your Age and Location Impacts Your Risks of Identity Theft
News reports may often give the impression that mostly older Americans are at the greatest risk of identity theft and…

10 Steps to Protect Your Laptop and Data from Theft
a third of Americans have been the victim of identity theft; that’s 15 million people (about twice the population of…

How to Prevent Identity Theft While on Vacation
Whether you’re planning an adventure to the far-flung corners of the world or a quick trip to a nearby hotspot,…

Alternative Loan Monitoring
If you rely on your credit report to show all loans that have been taken out in your name, you’re…

Setting Up Your IDSeal Account
IDSeal’s all-in-one subscriptions include so many helpful identity theft and device protection features for an incredible price, and we don’t want…

Spam Calls & Scam Calls
Scam calls are nothing new, but like other criminal activities, they are becoming more sophisticated, which means that we must…

My Wife Is a Zombie
I’m sure you’re wondering what I mean when I say that my wife is a zombie, and it’s a story…

How To Use Credit Freezes & Fraud Alerts
In a world where fraud and identity theft run rampant and methods for protecting your credit file are many, it’s…

Social Media Check-In
June 30th is World Social Media Day, which is a day designated for celebrating all of the relationships that have…

The Best Protection When Fighting Malvertising
Did you know that anyone who sees an ad on the internet is at risk for a malvertising attack? Malvertising is a tactic that…

Getting Started with Financial Transaction Monitoring
IDSeal recently released a new feature to its identity theft protection suite: Financial Transaction Monitoring. Utilizing this feature will help you stay…

Cybercriminals Target Children for Identity Theft
Yes, you read that right. Children have been, and continue to be, targets of cybercriminals for identity theft. You may…

To QR or Not To QR
QR codes (i.e. Quick Response codes) have been around since the 1990’s with widespread use beginning in the early 2000’s.…

Two New Features Now Available!
Great News! IDSeal gave the Member Portal a facelift. Better yet? Two new features have been added: Financial Transaction Monitoring…

Facial Recognition Software: the Good and the Bad
In general, facial recognition is one of the most sacred forms of PII (personally identifiable information.) Like any other form…
The Rising of BEC & EAC
Criminals hacking into email accounts isn’t anything new. This particular scam, BEC (Business Email Compromise) & EAC (Email Account Compromise),…

IDSeal Pro-Tec for macOS
We’ve got big news! IDSeal Pro-Tec is now available as a desktop application for macOS devices, with more features than…
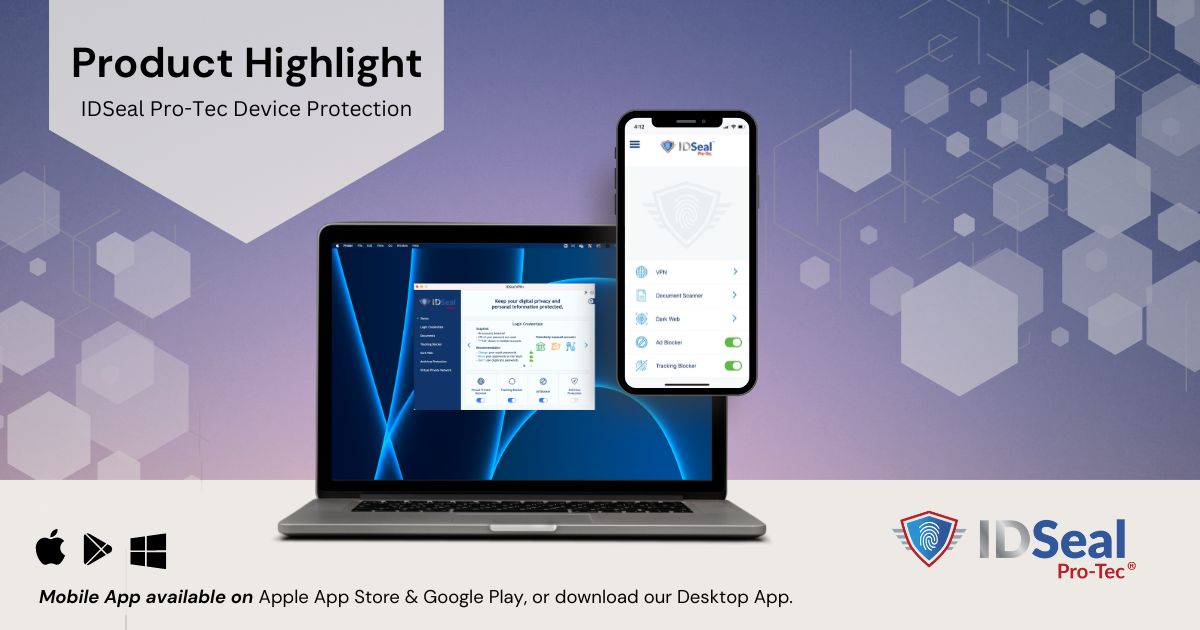
What Is IDSeal Pro-Tec?
IDSeal Pro-Tec is our proprietary device security and online safety solution that combines 14 industry leading features in one application…

Dark Web Breakdown
Did you know that what we see on the internet is just the tip of the iceberg? The internet that…

What Is Your Social Security Number?
Let me paint you a picture: you are sitting in your doctor’s office. The nurse hands you a form to…

Ransomware: What is it and How to Protect Yourself Against it
Ransomware is one of the fastest-growing threats to cybersecurity, and it doesn’t seem to be slowing down anytime soon. According…

Protect Your Identity From Holiday Grinches
With the holidays around the corner and more people heading online and in stores to do their shopping, it is…

Don’t Let Online Scammers Ruin Your Holidays
As the holiday season swiftly approaches and more individuals are turning to do their shopping online this year, it’s important…

Trick, or Treat? Don’t Get Tricked Out Of Your Reward Program Treats
There are a lot of benefits to giving up your information. You could get a free sandwich from your favorite…

Build-An-Identity: How Cybercriminals Create a Brand New Person
Do you know those stores your kids always want to go to where they get to build a stuffed animal,…

The Only Thing You Need To Know About Identity Theft
There are a lot of lists and searches you can do that will tell you the things you need to…

College Student Identity Theft and Fraud
Identity thieves love to prey on vulnerable people and, as crazy as it sounds, college students are high up on…

Your Child’s Identity: Stolen at Birth
Child identity theft is when a cybercriminal steals the identity of a child under the age of 18. It is…

Avoiding Social Engineering and the Psychological Con Artist
In a lot of ways, identity theft and fraud are very impersonal attacks; fraudsters hack into databases to find and…
Identity Theft and Social Media Hazards
Amazon, Fortnite, Netflix, Facebook, Spotify, and Tik Tok. What do all of these things have in common? The answer: more…

How to Avoid Becoming a Victim of a Fraudulent Charity
We all want to help out when we are willing and able. When it comes to natural disasters, epidemics, children…

Make Sure You Are Applying For a Job, Not For a Scam!
Whether you are a recent graduate looking for that first job, or maybe you have decided it was time for…

Your Home Can Be Your Work’s Biggest Threat
Working from home has a lot of perks. You don’t have to wear a tie, no worries about anyone stealing…

You’re Not The Only One Who Can File Your Taxes
Tax season is here, and that means while you are taking time to file your return and receive a refund,…

IDSeal Traveling Blog
Spring Break. Family Vacation. Solo Wanderlust. Local Stay-cation. No matter what type of break you take, we all need to get…

2019 Data Breach Year in Review: The industries hit the hardest, the people impacted, and the personal data put at risk
Although 2019 has come to a close, the wide-spread effects of the data breaches that made headlines during the year…

Identity Fraud From Space
In August 2019, we were captivated by that idea after the accusations of identity fraud in space made headlines. During…

Why Hackers Hate ID-Theft Protection | From a Fictional Hacker’s Perspective
There are plenty of people out there whose identities have no protection at all. I’ve never been that kind of…

Helpful Tips To Secure Your Phone
Just like your computer, the first step to protecting your phone from attacks is making sure you consistently update your…

3 Questions Answered About Identity Theft Protection
Identity theft has evolved over the years. As devices became smarter, access to everything from personal documents to personal data…

Why You Should Protect Your Child’s Identity From Thieves Today
An NBCNews.com report recently revealed that 1 million American kids had their ID stolen in 2017. The result: $2.67 billion…
Get the latest from IDSeal's News and Blog straight to your inbox. Subscribe now!