
Organization Description: The Pennsylvania State Education Association (PSEA) is the largest public employee union in Pennsylvania, representing teachers and education professionals across the state.
Breach Size: 500,000 people
Data Exposed: PSEA suffered a data breach in which hackers gained unauthorized access to sensitive files stored on its network. The compromised data includes full names, Social Security numbers, and in some cases, home addresses and financial account details. The breach went undetected for months.
Organization Description: Lafayette Federal Credit Union is a Maryland-based financial institution serving members nationwide with banking, loans, and credit services.
Breach Size: Over 75,000 people
Data Exposed: Lafayette Federal Credit Union experienced a data breach after hackers exploited a vulnerability in its third-party file transfer software, MOVEit. The incident exposed sensitive data including names, Social Security numbers, financial account information, and other personal details. The breach was part of a larger campaign targeting MOVEit users.
Description: VF Outdoor is the parent company of several major apparel brands, including The North Face and Timberland, known for outdoor and lifestyle clothing and gear.
Breach Size: 15,713 people
Data Exposed: VF Outdoor disclosed that The North Face and Timberland experienced a massive data breach that went undetected for nearly two years. Hackers accessed 15,713 customer accounts using stolen credentials. Exposed data includes full names, usernames, email addresses, phone numbers, and purchase histories. Although no passwords or payment card information were exposed, VF has notified affected customers.
Organization Description: WK Kellogg Co is a leading U.S. food manufacturer known for producing popular cereal brands such as Frosted Flakes, Froot Loops, and Corn Flakes.
Breach Size: Undisclosed
Data Exposed: WK Kellogg Co confirmed a data breach that exposed sensitive personal information, including names, addresses, and Social Security numbers. The breach was carried out by the Clop ransomware group, which accessed files containing employee data. Although the company has not confirmed the total number of individuals impacted, they are notifying affected parties.
Organization Description: Laboratory Services Cooperative (LSC) is a nonprofit organization that offers centralized laboratory services to its affiliated members, including certain Planned Parenthood centers.
Breach Size: 1.6 million people
Data Exposed: LSC has exposed the health data of approximately 1.6 million individuals. The breach resulted from a misconfigured cloud storage system, leaving sensitive information — including lab test results, patient names, dates of birth, and contact details — accessible without proper authentication.
Organization Description: Blue Shield of California is a not-for-profit health plan that offers a variety of health insurance plans to Californians.
Breach Size: 5,498 people
Data Exposed: Blue Shield of California recently disclosed a data privacy incident involving the improper configuration of Google Analytics, inadvertently shared with Google Ads. While the incident was only recently discovered, this took place between April 2021 and January 2024. This information may have been used to target members with personalized ad campaigns. Impacted data includes insurance details, claim service dates, provider names, patient names, and patient financial responsibility.
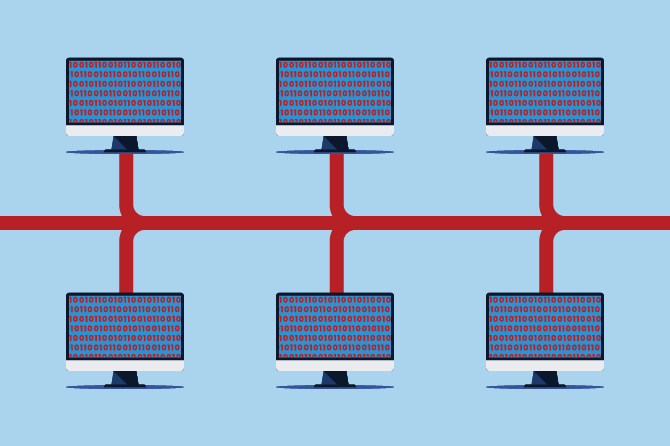
A Botnet is a group of internet-connected devices infected with malware and controlled by a hacker without the owners’ knowledge. These devices, often called “bots,” can be used to send spam, steal data, or launch large-scale attacks like Distributed Denial of Service (DDoS). A well-known example is the Mirai botnet, which hijacked security cameras and routers to crash major websites like Twitter and Netflix in 2016. Botnets can turn everyday devices into powerful tools for cybercrime if not properly secured.

A Zero-Day Exploit is a cyberattack that takes advantage of a software vulnerability that is unknown to the software maker or has no official fix yet. Because there’s no patch or defense available at the time of the attack, zero-day exploits are highly dangerous and often used by hackers to steal data, install malware, or take control of systems. For example, in 2021, hackers used a zero-day flaw in a Microsoft Exchange Server to access thousands of email accounts worldwide before a patch was released, highlighting how quickly attackers can strike before defenses are in place.
The rise in recent data breaches shows just how relentless cybercriminals have become in their quest to access personal and financial information. Whether it's a school, a bank, or a well-known brand, no organization is immune — and that means individuals are at risk. While practicing good cyber habits like using strong passwords and avoiding suspicious links is important, it's not always enough. That’s why IDSeal® offers identity theft protection that goes beyond prevention. From real-time monitoring and instant alerts to 24/7 Identity Theft Recovery Support, IDSeal is here to help you respond quickly and confidently if your information is ever compromised.
Stay connected with us on social media for the latest updates on data breaches and cybersecurity threats as they happen. Don’t wait to become a victim — start protecting your identity now!

Major Data Breaches & Hacking News in June 2024

IDSeal® allows you to independently manage your identity
Start protecting your identity today! Signing up is quick & easy
Remember, 1-in-4 Americans are the victim of identity theft. It's not a matter
of if you'll become a victim, it's when...